Entri yang Diunggulkan
- Get link
- X
- Other Apps
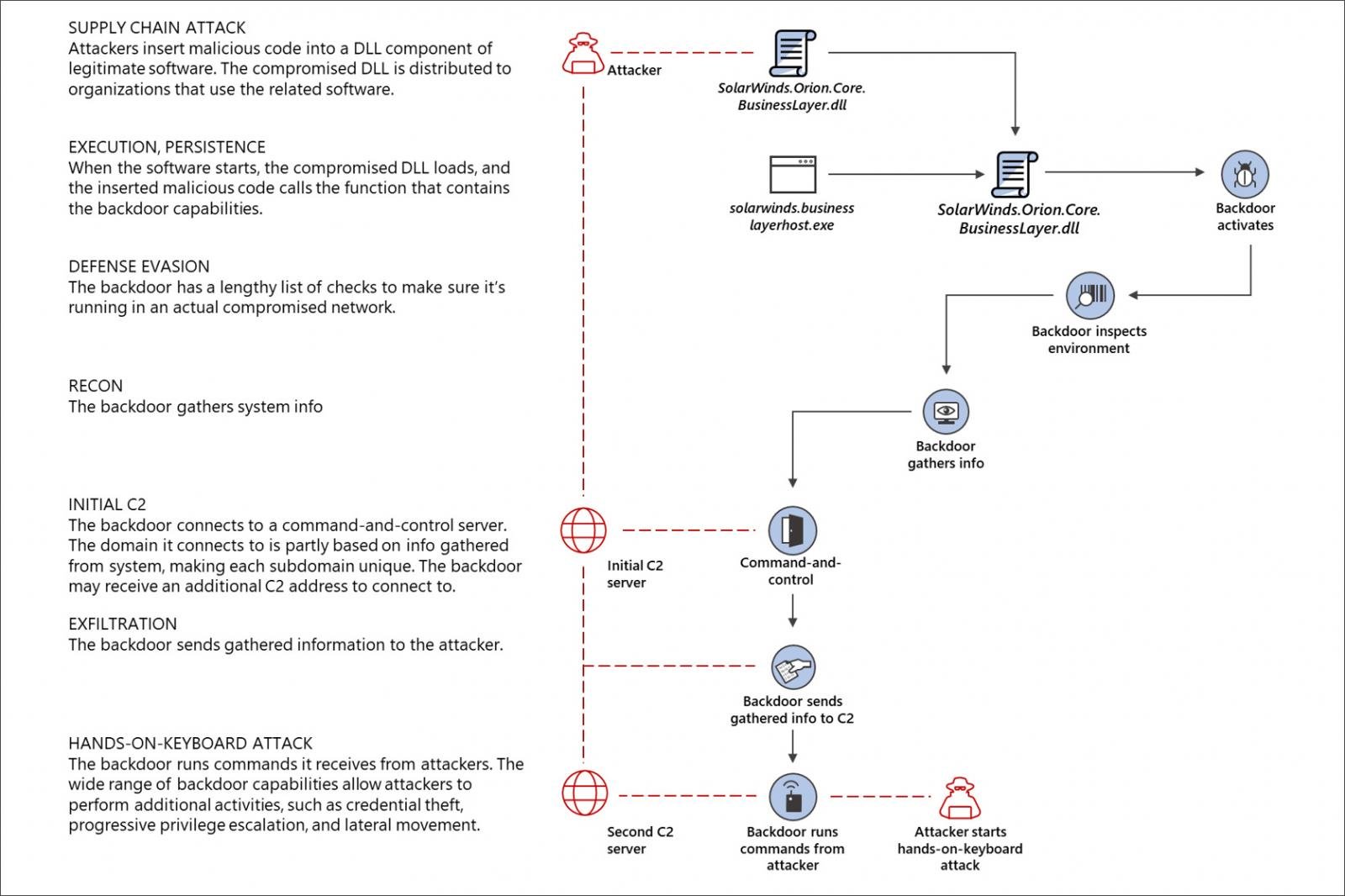
Texas-based IT management company SolarWinds on Friday shared more information on the impact of the significant breach disclosed late last year and claimed that less than 100 of its customers were actually hacked. Cybersecurity company FireEye discovered the supply chain attack against the SolarWinds products while investigating a compromise of their own network and publicly announced the discovery of the SUNBURST backdoor on 13 December 2020.
 Solarwinds Is The Tip Of The Iceberg Help Net Security
Solarwinds Is The Tip Of The Iceberg Help Net Security
SolarWinds uses a digital code-signing certificate to digitally sign each software build and to help end users authenticate the code comes from us.

Solarwinds security breach. As such SolarWinds has determined that the credentials using this password had nothing to do with the. With SolarWinds believing as many as 18000 of its customers had been affected by the breach as that was the number that had downloaded the malicious update Ramakrishna explained that in the immediate aftermath the SolarWinds security team looked to contact everyone possible to try to address their concerns and questions. Hacked firm issues urgent security fix 24 December 2020 Network tools specialist SolarWinds has updated its flagship Orion software 11 days after revealing a major breach.
The group responsible was able to infect legitimate SolarWinds Orion software patches with malware now known as SUNBURST. A SolarWinds third-party public relations spokesperson. But for security and software vendors specifically if youve succumbed to the temptation of producing opportunistic marketing - Ive seen some egregious Want to avoid a breach like SolarWinds.
Confirmed compromises have occurred dating back to March of 2020. The ongoing breach affecting thousands of organizations that relied on backdoored products by network software firm SolarWinds may have jeopardized the privacy of countless sealed court documents. Earlier this year malware was inserted into a software update for SolarWinds Orion product.
On December 11 th 2020 the US. Before FireEye discovered that over 300 of its proprietary cybersecurity products had been stolen the breach went undetected for an estimated nine months during which hackers gained access to state secrets and intellectual property including Black Start a technical blueprint for how the US. SolarWinds Orion is a commonly used network management software stack used to manage complex.
Many things came together to crack SolarWinds but it may all have started with that classic mistake of leaking a lousy password. As part of our response to the SUNBURST vulnerability the code-signing certificate used by SolarWinds to sign the affected software versions was revoked March 8 2021. Furthermore the third-party application did not connect with the SolarWinds IT systems.
This attack was conducted by a sophisticated and likely nation-state based attacker. Theres always learning in any crisis. For organizations at the end of the digital development and supply pipeline the SolarWinds security breach highlights the need to actively scan monitor and manage all software updates no matter.
Since SolarWinds has many high-profile clients including Fortune 500 companies and multiple agencies in the US government the breach could be massive. This is industry-standard best practice for. According to the companys estimations up to 18000 of their customers installed the update which gave the bad actors access to their networks.
And we were no exception Gareth Corfield Tue 11 May 2021 1959 UTC. A second cyber-security company breached during the SolarWinds supply chain attack also came to light this week in a Forbes article that covered the research work of Erik Hjelmvik founder of. Government and the company SolarWinds disclosed a breach into their SolarWinds Orion Platform network management software.
Microsoft president Brad Smith said in a. FireEye a 35 billion cybersecurity company known for identifying culprits in some of the worlds biggest data breaches was one of the customers affected by the attack. Plans to restore power in the event of a cataclysmic.
SolarWinds CEO describes overhauled Orion build system after that very small unique security breach This can happen to anybody. CyberUK 21 SolarWinds chief exec has described the 18000 customers who downloaded backdoored.
 Gastbeitrag Cybertrap Solarwinds Security Breach Anovis
Gastbeitrag Cybertrap Solarwinds Security Breach Anovis
 Solarwinds Update On Security Vulnerability Orange Matter
Solarwinds Update On Security Vulnerability Orange Matter
 What Do We Know About The Solarwinds Hack Financial Times
What Do We Know About The Solarwinds Hack Financial Times
 Solarwinds Supply Chain Hack Responsible For Fireeye Breach Secplicity Security Simplified
Solarwinds Supply Chain Hack Responsible For Fireeye Breach Secplicity Security Simplified
 Solarwinds Orion Hack December 2020 Youtube
Solarwinds Orion Hack December 2020 Youtube
 The Great Hack Attack Solarwinds Breach Exposes Big Gaps In Cyber Security Financial Times
The Great Hack Attack Solarwinds Breach Exposes Big Gaps In Cyber Security Financial Times
 Solarwinds Hacked Firm Issues Urgent Security Fix Bbc News
Solarwinds Hacked Firm Issues Urgent Security Fix Bbc News
 Solarwinds Software Security Breach What To Know Icma Org
Solarwinds Software Security Breach What To Know Icma Org
 The Solarwinds Cyberattack The Hack The Victims And What We Know
The Solarwinds Cyberattack The Hack The Victims And What We Know
 Solarwinds Orion Security Breach Cyberattack Timeline And Hacking Incident Details
Solarwinds Orion Security Breach Cyberattack Timeline And Hacking Incident Details
 A Moment Of Reckoning The Need For A Strong And Global Cybersecurity Response Microsoft On The Issues
A Moment Of Reckoning The Need For A Strong And Global Cybersecurity Response Microsoft On The Issues
 Us Govt Fireeye Breached After Solarwinds Supply Chain Attack
Us Govt Fireeye Breached After Solarwinds Supply Chain Attack
 Microsoft A 2nd Group May Have Also Breached Solarwinds
Microsoft A 2nd Group May Have Also Breached Solarwinds
 What You Need To Know About Solarwinds Orion Security Breach Volico
What You Need To Know About Solarwinds Orion Security Breach Volico
Comments
Post a Comment